Recovering your Vault Master Seed
In this article we describe how the Vault master seed is computed from the three shared-owners’ individual seeds, and how you can recover it at any time from the three shared-owner recovery phrases.
Details of the procedure are provided mainly for transparency and educational purposes. In case of recovery, it is highly recommended to recompute your master seed offline on a Ledger Nano device, following the procedure described here.
Summary
- The Vault master seed is derived from the three shared-owners individual seeds using the BIP39 and BIP32 open standards.
- In recovery scenarios, the Vault master seed and master key can be recomputed from the three Shared Owners recovery phrases using open source tools and can be used to reseed another wallet.
Generation of BIP39 seeds from shared-owner PSDs
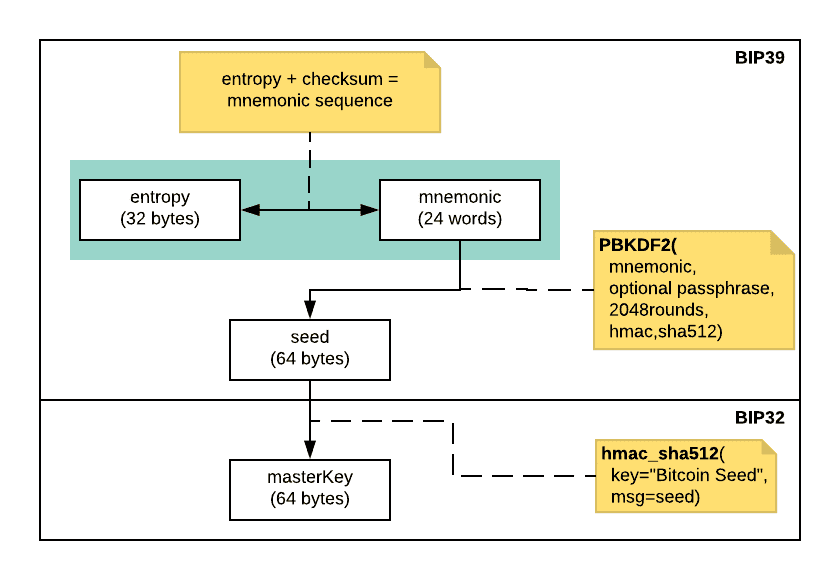
During the key ceremony, each Shared Owner’s PSD generates a unique 256-bit entropy sequence using the device’s True Random Number Generator. Following BIP39, each 256-bit entropy sequence is encoded into a 24-word recovery phrase that is displayed on the device and stored by the shared-owner on a cryptosteel for recovery scenarios. A unique 512-bit BIP39 seed is then derived from each Shared Owner’s 256-entropy sequence using the PBKDF2 algorithm.
Remark: As part of BIP39, when applying PBKDF2 to derive a seed, an optional passphrase can be provided as input to the algorithm. During the Vault’s derivation process, no passphrases are used.
For a single seed wallet, at this stage the wallet master key would finally be derived from the BIP39 seed using the HMAC-512 algorithm. For the Vault, the process is slightly different and the next section describes how the Vault master seed is derived from the three shared-owners’ individual seeds.
Deriving master seed fragments
Three master seed fragments are derived from the three Shared Owner individual seeds using BIP32:
- Each shared owner 512-bit BIP39 seed is first derived into a master key following the BIP32 standard.
- A master seed fragment is then obtained from each shared-owner BIP32 master key by computing the 512-bit derived key corresponding to the custom derivation path m/VLT’/KEY’.
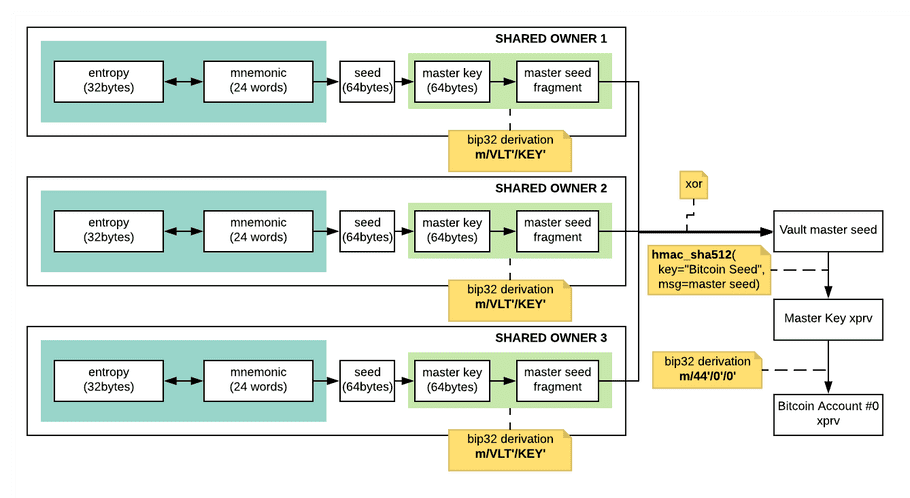
Combining master seed fragments
Finally, the three derived master seed fragments are XORed together to produce the Vault unique master seed.
Remark: The XOR operation is performed on the Vault’s HSM after the three Shared Owners’ seeds have been transferred from the PSDs to the HSM through a secure cryptographic channel. This ensures that the master seed is kept secret, and that it never leaves the secure enclave of the HSM.
The Vault master seed is then used to compute the BIP32 Vault master key that corresponds to the root key of the wallet used to derive all accounts’ keys and addresses.
Remark: Because of the key derivation and the fact that PBKDF2 is a one way function, we cannot go backward and encode the Vault master seed into a BIP39 24-word recovery phrase.
Recomputing the Vault master seed and master key
Using the steps presented above, it is possible to recompute manually the Vault master seed from the shared-owners’ recovery phrases using open source libraries such as bip-utils.
Ledger also provides an open-source tool that can be used to directly recompute the Vault master seed and master key from the three recovery phrases.
Security recommendations
Again, it is not recommended to recompute your master seed yourself, and we advise following the default recovery procedure that uses a Nano S device (a recovery procedure is also possible with a Nano S Plus, as explained here). This method ensures that your master seed is generated offline and protected in the secure environment of the Nano device.
In case you need to recompute your master seed yourself, for example to re-seed another wallet, it is recommended to run the recovery operations offline, on an air-gap computer, and to never reconnect this machine until your funds have been fully transferred to a new cold wallet.